We recently patched a high risk security vulnerability in our Gatsby Cloud Image CDN service. Since all affected customers have been informed about the vulnerability, and have been given time to patch their sites, we are now communicating details of the vulnerability and our fix publicly.
Credit for finding this vulnerability goes to Shubham Shah of Assetnote and Sam Curry of Yuga Labs, who brought the issue to our attention.
Vulnerability Details
The Gatsby Cloud Image CDN implementation allowed for arbitrary URLs to be sent to the u= URL parameter, which was exposed as a query parameter on _gatsby/image and _gatsby/file/ routes. Due to insufficient checking if the URL was valid for a build, the content of the arbitrary URL would be rendered by the website, presenting an opportunity to exploit the vulnerability via a Server Side Request Forgery (SSRF) and/or Cross Site Scripting (XSS) attack.
While the _gatsby/image route and the u= parameter is used by sites not using our Image CDN service, the vulnerability only affected sites that had enabled the Image CDN.
We have no information that would suggest that this vulnerability had been used to target our customers.
How we addressed this vulnerability
On September 21st we released an update to gatsby-plugin-utils@3.17.1, and on October 6th an update to the Gatsby Cloud, which together will fully mitigate the vulnerability.
Sites that are using our Image CDN service and running a non-vulnerable version of gatsby-plugin-utils will now have all CDN URLs encrypted as part of the build process, through the query parameter eu=. The encryption mechanism ensures that only valid URLs that were included in a site build will be interpreted as a valid route. An added benefit of this approach is that the source URL is no longer exposed client side, which builds a layer of privacy for our customers running a private headless CMS.
What you should do to keep your website(s) safe…
To remediate the vulnerability for your site(s), choose one of the following options:
- Remediation Option 1: Upgrade to
gatsby-plugin-utils@3.17.1or higher by upgrading Gatsby to the latest version, and rebuild your site. Once rebuilt and deployed your site will no longer be vulnerable to the flaw.To upgrade, we recommend taking the following steps:- Bump all
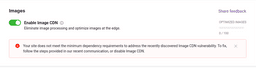
gatsby-*packages (and gatsby) to the latest versions and commit these to your site source repository. (As an example, run:npm i gatsby@latest gatsby-transformer-sharp@latest gatsby-source-contentful@latest.) - Navigate to “Site Settings” > “Images”. With Image CDN enabled, check the message that will indicate if your site is vulnerable or not vulnerable. (If you don’t see this message, reload the page in your browser.) The message will only be displayed when Image CDN is enabled.
- In the case that your site is still vulnerable, use yarn/npm resolutions to force the installed version of
gatsby-plugin-utilsto>=3.17.1.
- Bump all
Indication that your site is vulnerable.
Indication that your site is not vulnerable.
Please note that you may need to wait a second for the message to update as the vulnerability check is run.
- Remediation Option 2: Disable Image CDN for your site(s). Since this vulnerability only affects websites that have Image CDN enabled, disabling the feature will eliminate vulnerability. Please note that disabling Image CDN will trigger a full rebuild of your site. Once rebuilt and deployed your site will no longer be vulnerable to the flaw.
If you have any additional questions please feel free to reach out to our Customer Success team at support@gatsbyjs.com or directly to our security team at security@gatsbyjs.com.